Hardware Accelerated Cold-Boot Attacks
Abstract
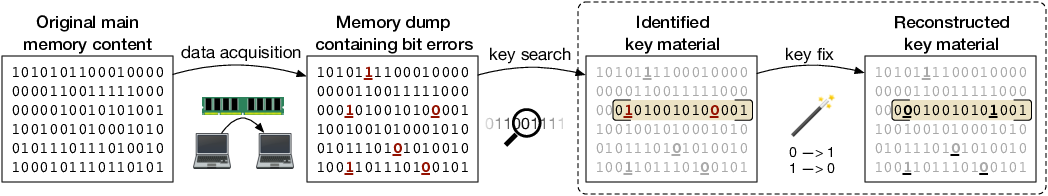
Cold-boot attacks exploit the fact that DRAM contents are not immediately lost when a computer system is powered off. Instead the contents decay rather slowly, in particular if the DRAM chips are cooled to low temperatures. This effect opens an attack vector on cryptographic applications that keep decrypted keys in DRAM. An attacker with access to the target computer can reboot it or remove the RAM modules and quickly copy the RAM contents to non-volatile memory. By exploiting the known cryptographic structure of the cipher and layout of the key data in memory the resulting memory image can be searched for sections that could correspond to decayed cryptographic keys. Then, the attacker can attempt to reconstruct the original key. However, the runtime of these algorithms grows rapidly with increasing error rate and complexity of the bit error model (non-idealized asymmetric decay), which limits the practicability of the approach in software.
In this project, we study how the algorithms for key search (streaming, [Rie13]) and key reconstruction (recursive branch-and-bound, [Rie14]) can be accelerated with custom computing machines. We present several FPGA-based architectures that accelerate cold-boot attacks for AES encrypted data. As special features, we A) explore hardware workers that autonomously cooperate using work stealing to allow parallel execution and full utilization of the target FPGA, B) show the advantages of instance-specific designs that target a specific hard problem instance to improve performance and finally, we C) demonstrate how instance-specific designs can be generated just-in-time such that the provided speedups outweigh the additional time required for design synthesis [Rie17].
Source Code
Source code of our software and hardware implementations as well as our evaluation data and a demo application are available online at github.com/pc2/coldboot.
Publications
Keywords
cold-boot attacks; key reconstruction; key find; AES; key schedule; branch-and-bound; FPGA; Field programmable gate arrays; hardware acceleration; work stealing in hardware; instance-specific computing; just-in- time synthesis; on-demand synthesis; cryptographic applications; bit error model; Maxeler dataflow computing system; open-source